Ever wondered, “Where is my Google account logged in?” If you’re concerned about your account’s security or just curious about where you’ve logged in, we’re here to help. In this comprehensive guide, we’ll explore how to check your Google account activity, manage devices, and enhance your security to keep your information safe.
Why Knowing Where Your Google Account Is Logged In Matters
Our Google accounts are gateways to a vast array of personal information—emails, photos, documents, and even financial data. Understanding where our Google account is logged in is crucial for several reasons:
- Security: Unauthorized access to our account can lead to data breaches or identity theft. By knowing where we’re logged in, we can quickly spot and address any suspicious activities.
- Privacy: Ensuring that only trusted devices have access protects our personal information from prying eyes.
- Device Management: Over time, we might log in on multiple devices—some we no longer use. Regularly checking logged-in devices helps us manage and remove old or lost devices.
How to Check Where Your Google Account Is Logged In
Let’s delve into the various methods we can use to find out where our Google account is currently logged in. Whether we’re using a desktop or mobile device, Google provides straightforward ways to monitor account access.
Using a Desktop Browser
Step 1: Go to Your Google Account Page
Open your preferred web browser and navigate to the Google Account page. Ensure we’re signed in with the Google account we want to check.
Step 2: Access the Security Section
On the left-hand sidebar, click on Security. This section houses all settings related to account protection.
Step 3: Find Your Devices
Scroll down to the Your devices section. Here, we’ll see a brief list of devices where our Google account is currently signed in.
Step 4: Manage Devices
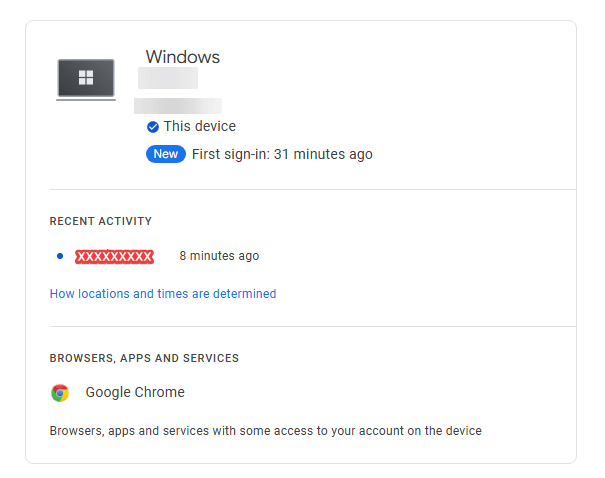
Click on Manage devices. This action will display all devices, along with details like device model, location, and last activity.
Step 5: Review Device Details
For each device, we can:
- See Device Type: Identifies whether it’s a phone, tablet, or computer.
- View Location: Based on IP address, shows where the device was last active.
- Check Last Accessed: Shows when the device last connected to our account.
Using the Google Account Page on Mobile
If we’re on a mobile device without the Google apps, the mobile browser is an excellent option.
Step 1: Open Your Mobile Browser
Launch Safari, Chrome, or any browser on our mobile device and go to myaccount.google.com.
Step 2: Sign In
Ensure we’re signed in to the correct Google account.
Step 3: Navigate to Security
Tap on the Menu icon (three horizontal lines) if needed, and select Security from the options.
Step 4: Check Your Devices
Under Your devices, tap Manage devices to view the full list.
Using the Gmail App
The Gmail app provides a convenient way to access our account settings.
Step 1: Open the Gmail App
Launch Gmail on our mobile device.
Step 2: Access Account Settings
Tap on our profile picture in the top-right corner and select Manage your Google Account.
Step 3: Go to Security
Swipe through the tabs and tap on Security.
Step 4: Review Devices
Under Your devices, tap Manage devices.
Using the Google Account App (If Available)
If we have the Google Account app:
- Open the App: Sign in if necessary.
- Navigate to Security: Similar to the Gmail app.
- Manage Devices: Review the list of devices.
Managing Devices Logged Into Your Google Account
Once we’ve identified where our Google account is logged in, it’s important to manage these devices effectively.
Reviewing Device Activity
Regularly reviewing our device activity helps us stay on top of our account’s security.
- Familiarize with Devices: Recognize all devices listed. Pay attention to device names and locations.
- Check Last Active Dates: Ensure the last activity aligns with our usage patterns.
- Look for Anomalies: Unusual locations or devices could indicate unauthorized access.
Removing Unrecognized Devices
If we spot a device we don’t recognize:
Step 1: Select the Device
In the list under Manage devices, click or tap on the suspicious device.
Step 2: Sign Out
Choose Sign out. Google will immediately revoke access from that device.
Step 3: Confirm Action
A prompt may ask us to confirm. Proceed to ensure the device is signed out.
Step 4: Secure Our Account
It’s advisable to:
- Change Our Password: Choose a strong, unique password.
- Enable Two-Factor Authentication: Adds an extra layer of security.
Regular Maintenance
- Periodically Check Devices: Set reminders to review logged-in devices monthly.
- Remove Old Devices: Sign out from devices we no longer use or own.
Enhancing Your Google Account Security
Protecting our Google account goes beyond just managing devices. Implementing additional security measures fortifies our defenses against potential threats.
Setting Up Two-Factor Authentication (2FA)
Two-Factor Authentication adds an extra verification step when logging in.
Step 1: Access Security Settings
Navigate to the Security tab in our Google Account.
Step 2: Set Up 2FA
Under Signing in to Google, click on 2-Step Verification and then Get Started.
Step 3: Choose Verification Methods
We have several options:
- Phone Prompt: Approve login attempts from our smartphone.
- Text Message (SMS): Receive a code via SMS.
- Authenticator App: Use apps like Google Authenticator.
- Security Key: Use a physical USB or Bluetooth key.
Step 4: Complete Setup
Follow the on-screen instructions to finalize 2FA.
Regularly Updating Your Password
Strong passwords are a fundamental security measure.
- Create Complex Passwords: Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoid Common Words and Phrases: Steer clear of easily guessable passwords.
- Use Unique Passwords: Never reuse passwords across different accounts.
- Change Passwords Periodically: Regular updates reduce the risk of long-term breaches.
Utilizing Google’s Security Recommendations
Google often provides personalized security recommendations.
- Security Checkup: Use Google’s Security Checkup tool to identify potential issues.
- Review Security Alerts: Pay attention to emails or notifications about account activity.
Keeping Recovery Information Up to Date
Ensure our recovery phone number and email address are current.
- Access Recovery Options: In the Personal info tab, update our recovery methods.
- Benefits: Helps us regain access if we’re ever locked out and receive critical security alerts.
Additional Tips for Securing Your Google Account
Beyond the basics, there are several advanced strategies we can employ to bolster our account security.
Use a Password Manager
Password managers help us create and store complex passwords without the need to memorize them.
- Benefits:
- Enhanced Security: Generates strong, random passwords.
- Convenience: Autofills login credentials.
- Recommendations: Consider reputable password managers like LastPass, Dashlane, or 1Password.
Regularly Review Connected Apps and Services
Over time, we may grant third-party apps access to our Google account.
Step 1: Access Third-Party Access
In the Security tab, find Third-party apps with account access.
Step 2: Review and Remove
- Review Each App: Check what permissions each app has.
- Remove Unnecessary Access: Revoke access for apps we no longer use or trust.
Keep Software Updated
Ensure all devices accessing our Google account have up-to-date software.
- Operating Systems: Regular updates patch security vulnerabilities.
- Browsers and Apps: Update to the latest versions for enhanced security features.
Educate Ourselves on Common Threats
Being aware of common cyber threats helps us avoid them.
- Phishing Scams: Be cautious of emails or messages asking for personal information.
- Malware: Use antivirus software to protect against malicious software.
- Public Wi-Fi Risks: Avoid accessing sensitive information on unsecured networks.
Understanding Account Activity and Notifications
Staying informed about our account’s activity is crucial for early detection of potential security issues.
Customizing Notification Settings
We can choose how we receive security alerts.
Step 1: Go to Security Alerts
In the Security section, find Security alerts settings.
Step 2: Choose Alert Preferences
- Email: Receive alerts via our recovery email.
- Phone: Opt for notifications or texts.
- Both: For maximum awareness.
Viewing Recent Security Events
Google logs significant security events.
Step 1: Access Recent Security Events
Within the Security tab, click on Recent security events.
Step 2: Review Events
- Sign-in Attempts: See when and where logins occurred.
- Password Changes: Verify if and when passwords were changed.
- Recovery Information Changes: Check for unauthorized alterations.
Addressing Suspicious Activities
If we spot unusual activity:
- Follow Security Recommendations: Google may provide immediate steps.
- Secure Our Account: Change passwords and review recovery options.
- Consider Account Recovery: If locked out, use recovery methods to regain access.
Handling Suspicious Activities and Phishing Attempts
Cyber threats are ever-present, but with knowledge and vigilance, we can protect ourselves.
Recognizing Phishing Emails
Phishing emails attempt to trick us into revealing personal information.
- Check the Sender’s Email Address: Official Google communications will come from a Google domain.
- Look for Generic Greetings: Phishing emails often use “Dear User” instead of our name.
- Beware of Urgent Language: Threats of account closure are common tactics.
- Avoid Clicking Links: Hover over links to inspect the URL before clicking.
Reporting Suspicious Emails
If we receive a suspicious email:
- Don’t Reply: Avoid engaging with the sender.
- Report to Google:
- In Gmail, open the email.
- Click the three-dot menu and select Report phishing.
- Delete the Email: Remove it from our inbox.
Stay Updated on Scam Trends
Cybercriminals evolve their tactics.
- Follow Trusted Sources: Google’s Security Blog, cybersecurity news outlets.
- Participate in Webinars or Workshops: Enhance our knowledge about online safety.
Using Google’s Security Checkup Tool
Google’s Security Checkup provides personalized recommendations.
Step 1: Access the Tool
Visit the Security Checkup page.
Step 2: Follow the Guided Steps
The tool will walk us through:
- Recovery Information: Ensure phone numbers and emails are current.
- Connected Devices: Review all devices with account access.
- Third-Party Access: Check apps with access to our data.
- Recent Security Events: Identify and address any unusual activities.
Step 3: Implement Recommendations
- Resolve Issues: Follow prompts to fix security concerns.
- Update Settings: Adjust account settings as suggested.
The Importance of Regular Account Maintenance
Routine account maintenance is vital for ongoing security.
Set Calendar Reminders
- Monthly Security Checks: Schedule time to review settings and activity.
- Password Updates: Reminders every 3-6 months to change passwords.
Educate Family Members
If we share devices or accounts:
- Discuss Security Practices: Ensure everyone understands safe habits.
- Set Up Family Accounts: Use Google’s Family Link for shared devices.
Backup Important Data
Regular backups prevent data loss.
- Use Google Takeout: Export data from Google services.
- Store Backups Securely: Keep backups on encrypted drives or reputable cloud services.
Exploring Advanced Security Options
For those seeking heightened security measures, Google offers advanced features.
Google Advanced Protection Program
Designed for users at higher risk, such as journalists or officials.
Benefits:
- Strongest Account Security: Protects against targeted attacks.
- Physical Security Keys Required: Mandates security keys for sign-in.
Enrollment:
- Visit the Advanced Protection Page: Google Advanced Protection
- Follow Enrollment Steps: Set up security keys and adjust settings.
Account Activity Reports
Stay informed about how our account is used.
Step 1: Access Activity Controls
In the Data & personalization tab, select Activity controls.
Step 2: Review Various Activities
- Web & App Activity: See searches and browsing history.
- Location History: Check locations tied to our account.
- YouTube History: View watch and search history.
Step 3: Customize Settings
- Pause Tracking: Stop tracking certain activities.
- Manage Activity: Delete past activities as desired.
Staying Informed About Security Best Practices
The digital landscape is ever-changing. Staying educated helps us adapt.
Follow Google’s Security Blog
Google’s Online Security Blog provides updates on:
- New Security Features
- Threat Warnings
- Tips and Best Practices
Attend Webinars and Workshops
Google and other organizations offer free training:
- Cybersecurity Awareness Workshops
- Privacy Settings Tutorials
- Secure Password Creation Sessions
Join Online Communities
Engage with others to share knowledge:
- Forums: Participate in security forums like Reddit’s r/cybersecurity.
- Social Media Groups: Join Facebook or LinkedIn groups focused on online safety.
Conclusion
Discovering “where is my Google account logged in” is more than a simple check—it’s a vital step toward securing our digital identity. By regularly monitoring our account activity, managing connected devices, and implementing robust security measures, we can significantly reduce the risk of unauthorized access and protect our personal information.
Remember, online security is an ongoing process. Stay proactive, keep informed, and make use of the tools and resources available to us. Let’s take control of our Google account security today and enjoy a safer online experience.
FAQ
Q: How Can I Make Sure No One Else Has Signed In to My Google Account?
A: We might worry that someone else is using our Google account without permission. To make sure no one else has signed in to your account:
- Review Recent Security Activity: Go to the Security section of your Google Account. Under Recent security events, you can see any significant changes or logins.
- Check Logged-In Devices: In Your devices, you can see computers, phones, and tablets where your account is signed in. Look for any devices you don’t recognize.
- Sign Out Remotely: If you find an unfamiliar device, select it and click Sign out. This will revoke access from that device.
- Change Your Password: To ensure security, update your password. This prevents anyone with your old password from accessing your account.
Q: What Should I Do If Someone Else Is Using My Account?
In case you suspect that someone else has access to your account:
- Secure Your Account Immediately:
- Change Your Password: Create a strong, unique password.
- Enable Two-Factor Authentication (2FA): Adds an extra layer of security.
- Review Account Permissions:
- Check Connected Apps: Under Security, see which third-party apps have access to your account and remove any you don’t recognize.
- Verify Account Recovery Information: Ensure your recovery email and phone number are correct.
- Monitor Account Activity:
- Review Recent Activity: Look for unfamiliar logins or actions.
- Check Sent Emails: See if any emails were sent without your knowledge.
- Report Unauthorized Access: Visit Google’s Account Recovery page for guidance.
Q: How Can I See Which Computers Have Accessed My Account Recently?
To see computers and devices that have recently accessed your Google account:
- Access Your Device List:
- Navigate to your Google Account’s Security section.
- Under Your devices, click Manage devices.
- View Activity Details:
- Click on each device to see the last location and time it was used.
- Pay attention to any unfamiliar devices or locations.
- Remove Suspicious Devices:
- For any device you don’t recognize, select Don’t recognize this device? and follow the prompts.
Q: Can I Limit Access to My Account at a Certain Period of Time?
While Google doesn’t offer time-based access restrictions directly, we can take steps to control account access during specific periods:
- Sign Out from Devices: Before a certain period (like a vacation), sign out from all devices except the ones you’ll use.
- Use Guest Mode or Incognito Windows: When using shared or public computers during that time, use private browsing modes that don’t retain login information.
- Monitor Account Activity: During the period, regularly check your account activity to ensure no unauthorized access.
Q: What Steps Can I Take to Secure My Account if I Suspect Unauthorized Access?
If you believe your account’s security is compromised:
- Change Password Immediately: Update your password to something strong and unique.
- Enable Two-Factor Authentication: Turn on 2FA to require a verification code in addition to your password.
- Review Account Settings:
- Security Questions: Update or review them.
- Recovery Options: Ensure your phone number and recovery email are correct.
- Check for Unauthorized Activity:
- Emails: Look for emails you didn’t send.
- Drive and Photos: Check for unfamiliar files.
- Consider Account Recovery: Follow Google’s account recovery steps if necessary.
Q: How Do I Make Sure No One Else Has Accessed My Account Recently?
To confirm that no one else has accessed your account in the recent past:
- Review Security Events:
- In the Security section, check Recent security events for any unusual activities.
- Check Login History:
- While Google doesn’t provide a detailed login history, unusual devices or locations in Your devices can indicate access.
- Verify Emails from Google:
- Google sends alerts for new sign-ins or suspicious activities. Review your inbox for any such notifications.
- Audit Connected Apps:
- Under Third-party apps with account access, ensure only trusted apps are connected.
Q: Is There a Way to See Individual Account Activity Over a Period of Time?
Yes, you can get an overview of your account activity:
- Google Account Dashboard:
- Visit the Google Dashboard to see an overview of your Google services usage.
- Activity Controls:
- Under Data & privacy, select My Activity to view your activity on Google services.
- Download Activity Data:
- Use Google Takeout to download your data for detailed analysis.
Q: What Should I Do in Case I Find Suspicious Activity?
If you discover suspicious activity:
- Secure Your Account:
- Change your password and enable 2FA immediately.
- Sign Out of All Sessions:
- In Security, select Manage devices and sign out from all devices.
- Report to Google:
- Use Google’s Security Issue Report to notify them.
- Check Other Accounts:
- If you use similar passwords elsewhere, change them to prevent further unauthorized access.
Q: How Can I Ensure That an Individual Doesn’t Have Access to My Account?
To prevent a specific person from accessing your account:
- Change Passwords and Security Info:
- Update your password and security questions.
- Remove Account Access:
- Under Security, revoke access from any devices or apps the individual might have used.
- Avoid Sharing Credentials:
- Never share your login information, even with trusted individuals.
- Monitor Regularly:
- Keep an eye on account activity to catch any unauthorized access early.
Q: How Often Should I Check My Account Security?
Regularly reviewing your account security helps keep your information safe:
- Set a Regular Schedule:
- Check your account security settings every few months.
- Stay Alert for Notifications:
- Pay attention to emails or alerts from Google about account activity.
- Update Recovery Information:
- Ensure your recovery phone number and email are always up to date.
- Keep Software Updated:
- Use the latest versions of browsers and apps for improved security features.
Q: Can I See Where My Google Account Is Logged In?
Yes, absolutely! By following the steps we’ve outlined, we can easily find out where our Google account is logged in from any device.
Q: What Should I Do If I See an Unfamiliar Device?
If we notice a device we don’t recognize:
- Sign Out Immediately: Remove the device’s access from our account.
- Change Our Password: Secure our account with a new, strong password.
- Enable 2FA: Add an extra layer of security to prevent future unauthorized access.
- Review Recent Activity: Check for any suspicious activities or changes made to our account.
Q: How Can I Prevent Unauthorized Logins?
Preventing unauthorized access involves several proactive steps:
- Enable Two-Factor Authentication: This makes it significantly harder for attackers to access our account.
- Use Strong, Unique Passwords: Avoid using the same password across multiple services.
- Stay Vigilant: Regularly check our account activity and security settings.
- Beware of Phishing Attempts: Don’t click on suspicious links or provide personal information to unverified sources.
Q: Is There a Way to Get Alerts for Unusual Activity?
Yes, Google automatically notifies us of unusual activity:
- Email Alerts: We’ll receive emails for new device sign-ins or password changes.
- Device Notifications: Android devices may display notifications about account activity.
- Review Security Settings: In our account, we can adjust how and when we receive alerts.
IT Security / Cyber Security Experts.
Technology Enthusiasm.
Love to read, test and write about IT, Cyber Security and Technology.
The Geek coming from the things I love and how I look.