In this digital era, we are often surprised by the news of organisation has been hacked and their personal data breached and exposed in the Dark Web.
It makes you concerned about the security of your systems and the potential threats lurking in the dark web?
Introducing CyberSuite – the ultimate solution for testing your systems for vulnerabilities, investigating potential threats, and monitoring for your company’s data on the dark web. In this article, I will go through on CyberSuite reviews.
CyberSuite offers robust and comprehensive Security-as-a-Service solutions empowers businesses to identify, remediate, retest, and monitor the presence of security vulnerabilities efficiently and effectively, ensuring your resilience in the face of evolving cyber threats.
Pros
- Comprehensive Security services such as Pen-testing-as-a-Service (PTaaS) and Dark Web Searches-as-a-Service (DWSaaS)
- 24/7 continuous penetration testing and vulnerability discovery.
- Proactively scours the dark web, identifying stolen credentials, session cookies, and data.
- Single pane of glass view for your vulnerability data
- Reduced operational costs
- User-friendly interface
- Fast response from support
Cons
- No assets grouping
CyberSuite Reviews
CyberSuite is a cutting-edge Security as a service(Saas), designed to test your systems for vulnerabilities, investigate potential weaknesses, and even monitor for company data on the dark web.
With CyberSuite, you can proactively identify weaknesses in your security infrastructure, address potential threats before they escalate into disasters, and keep a watchful eye on any compromised company information circulating on the dark web.
It has two modules which are:
- CyberStrafe (Penetration Testing as a service)
- Dark Magic (In-Depth Dark Web Searches as a Service)
Cyberstrafe (Penetration Testing as a service)
Rely on their proficient and certified penetration testers to conduct an in-depth examination of your systems.
By employing a mix of sophisticated tools and methodologies, CyberSuite surpasses standard procedures to detect potential security risks that automated scans may overlook.
This is the essence of “Deep-Dive Manual Penetration Testing” feature.
Dark Magic (In-Depth Dark Web Searches as a Service)
CyberSuite provides businesses with the ability to detect compromised credentials that are available on the Dark Web.
It also helps in identifying any company systems that have been infected with malware, which could be secretly extracting their data and uploading it to the Dark Web.
Furthermore, this solution can locate data dumps from company system breaches that have ended up on the Dark Web.
In simpler terms, think of the Dark Web as a hidden part of the internet where stolen data often ends up.
CyberSuite acts like a detective, searching this hidden part of the internet for any signs of your business’s data or credentials.
If it finds anything, it alerts you, so you can take action to protect your business.
It’s like having a security guard who’s always on duty, protecting your business from the threats of the Dark Web.
CyberSuite Reviews: How To Get Started
To use this tool is very easy. Here’s how to get started:
- Go to CyberSuite and sign up.
- Once you signed up, they will create your account and whitelist your IP address to access to the portal.
- You will receive information to access the portal via email.
- Go to CyberSuite portal and login. Add your URLs or IPs.
- It will perform the scan. Wait for the reports to appear, charts to populate, and report to be downloaded.
CyberSuite Reviews: Analyzing The Findings
Once the scan is completed, you can start analyzing the findings and take necessary actions.
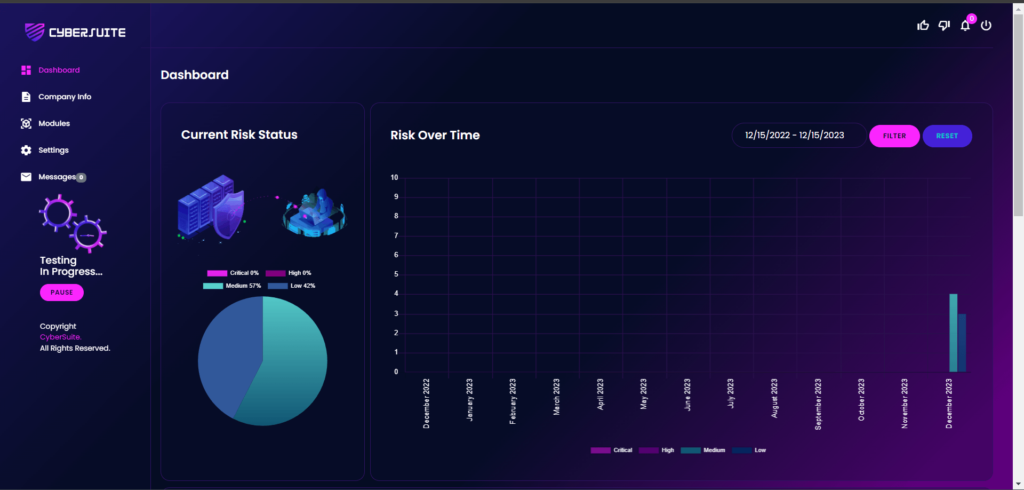
Dashboard
From the dashboard, you can see the overview or summary of Current Risk Status and Risk Over Time.
The Current Risk Status will show your current state into four(4) categorization which are Critical, High, Medium and Low.
At the right side of dashboard, is Risk Over Time which you can monitor monthly risk status.
Now, let’s go deeper on analyzing the findings. I will start on CyberStrafe, which is penetration testing module.
CyberStrafe
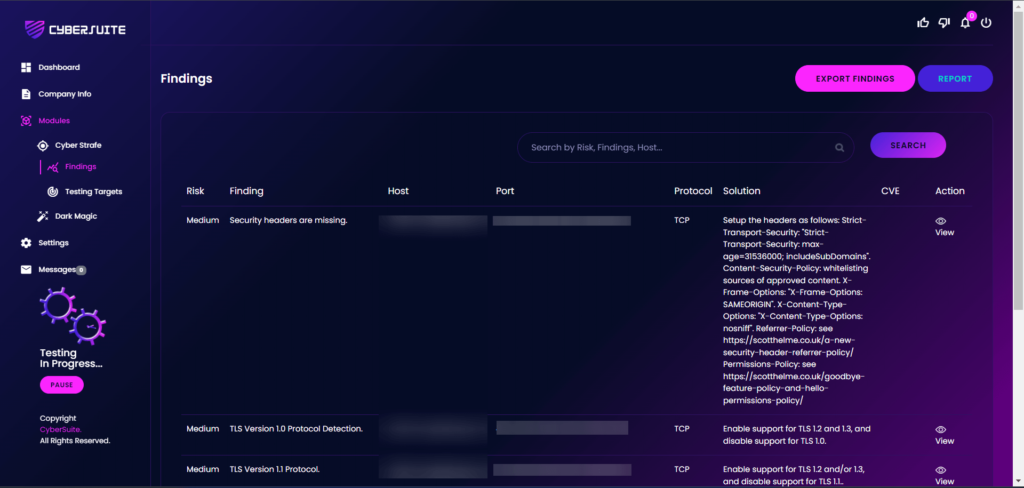
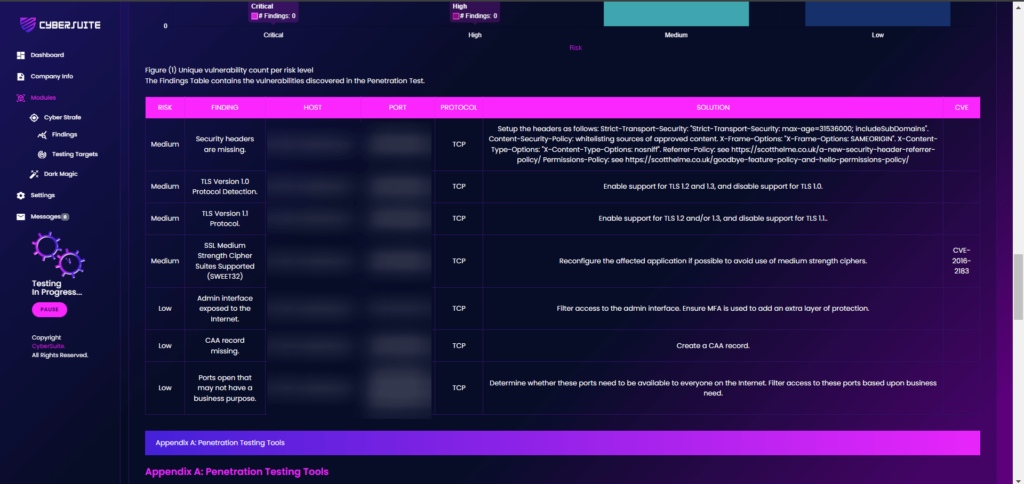
On the portal, go to Modules > CyberStrafe > Findings.
Right here, you can get the details on the findings, which host, ports, protocol, CVE and solution to rectify the findings.
On the solution part, it provided what you need to do to fix the findings.
With this, web administrator can easily close the findings as they will know what to do and which area should be reconfigured.
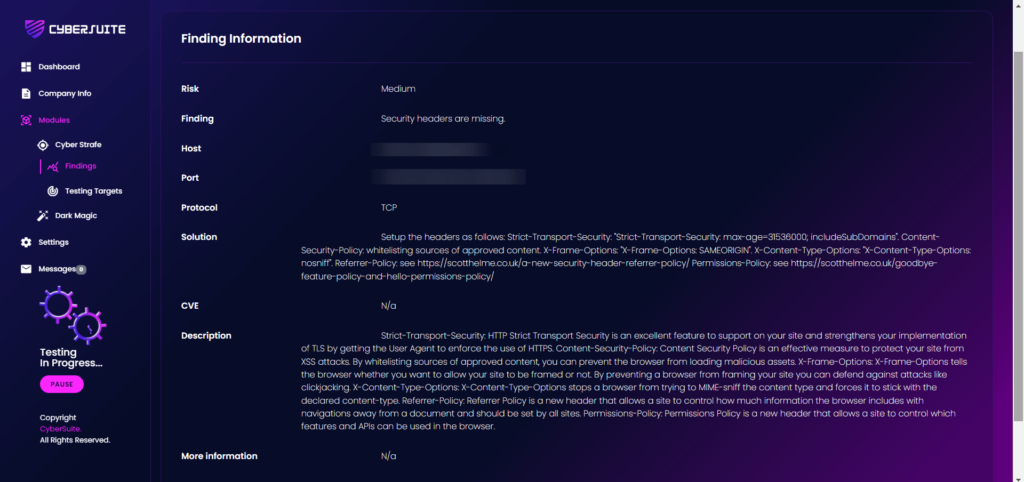
On the right side of the table, there is an Action column and there is a “View” button. Click on it.
It will show you in details on the specific finding where it added description info to understand more what’s the finding is about.
So that’s all about penetration testing report. Next, I’m going to walkthrough the Dark Magic features.
Dark Magic
Personally, this module kind of grab my attention as it could help any company, to discover there if is any credentials leaked or if any of the dark web user is talking about (or worst, announce target to) your company.
To find out about this, go to Modules > Dark Magic. Under Dark Magic, there are five(5) sections which are:
- Creds
- Company Data
- Radar
- Sessions
- Malware
Let’s go to each of the sections.
In the vast digital landscape, data breaches at third-party services can inadvertently expose your company’s credentials, posing a significant security risk.
“Creds” diligently monitors these breaches and identifies if any of the compromised credentials are associated with your company’s domain.
If such a correlation is found, “Creds” promptly alerts you, allowing you to take immediate action. This could involve resetting passwords, strengthening security protocols, or notifying the affected parties.
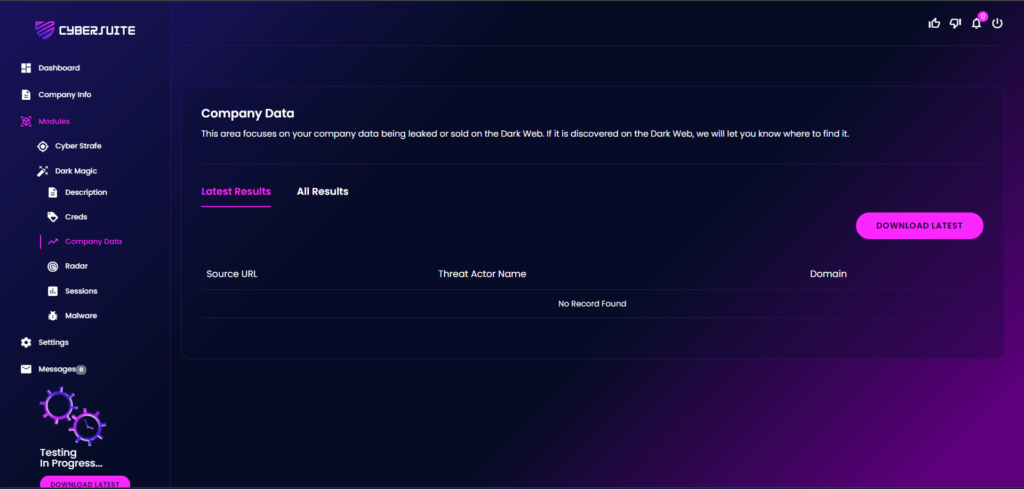
“Company Data” is operates by continuously scanning the Dark Web for any instances of your company’s data being leaked or sold.
If such an unfortunate event occurs, and your data is found to be compromised, the Company Data feature will promptly detect this.
The leaked data will be displayed in the dedicated interface of the tool, providing you with source of URL, Threat Actor Name and Domain.
This feature is crucial in today’s digital age, where data breaches are becoming increasingly common.
By alerting you to any leaks as soon as they happen, it allows you to respond swiftly and take necessary actions to mitigate the damage and protect your company’s reputation.
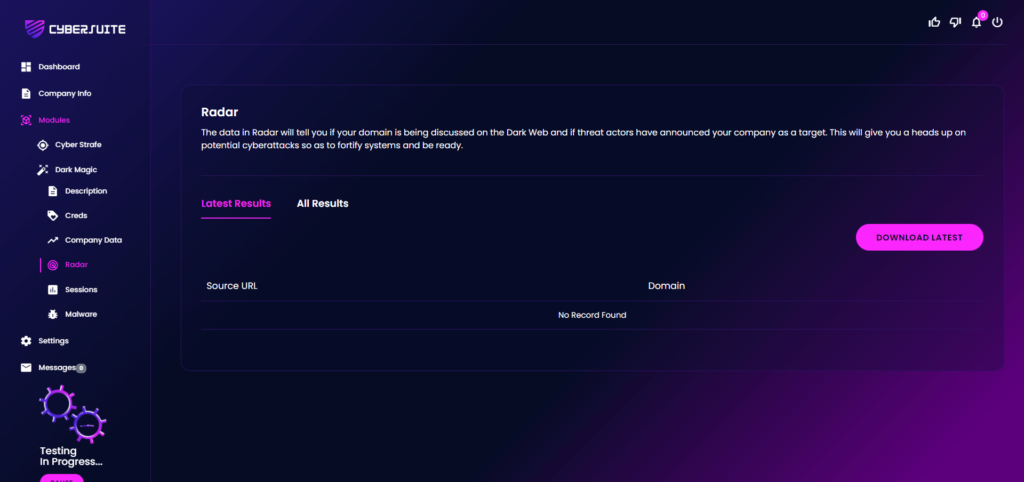
“Radar” serves as a vigilant watchman in the vast expanse of the Dark Web. It continuously monitors and alerts you if your domain name surfaces in Dark Web discussions.
This could be an indication that your domain is being scrutinized or exploited by threat actors.
Moreover, Radar also keeps an eye out for any explicit threats made against your company.
If cybercriminals have declared your organization as a potential target, Radar will promptly shows the findings on the portal.
This allows you to take proactive measures to bolster your security defenses and mitigate potential cyber threats.
The “Sessions” feature is a critical component that concentrates on session tokens, which have been intercepted from devices infected with malware.
In the complex world of cybersecurity, malware can infiltrate devices and sniff out session tokens, which can then be exploited by cybercriminals.
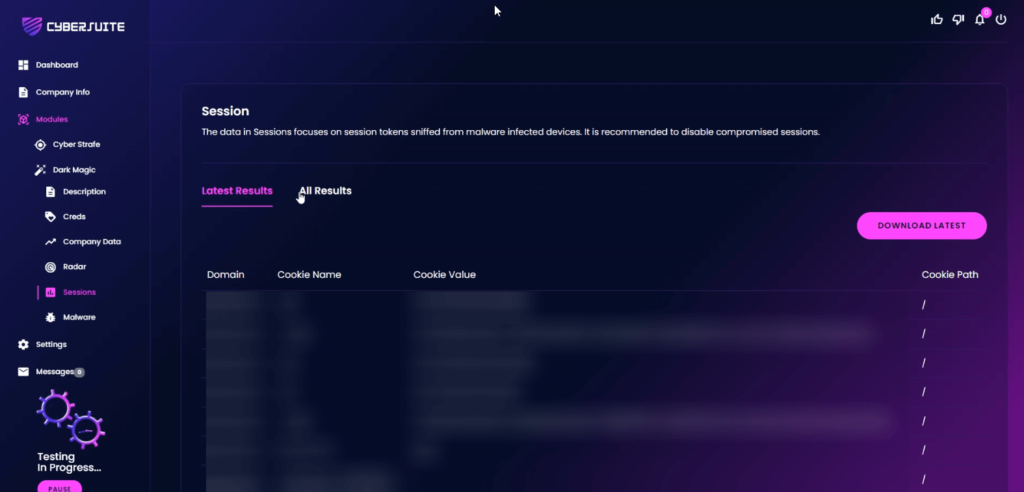
These session tokens are like digital keys, providing access to specific user sessions.
If they fall into the wrong hands, they can be used to gain unauthorized access to sensitive information.
The Sessions feature continuously monitors for such compromised session tokens related to your company.
If it detects any, it will promptly alert you.
Upon receiving such an alert, it is highly recommended to immediately disable the compromised sessions.
This swift action can prevent unauthorized access and potential data breaches, thereby maintaining the integrity of your company’s digital environment.
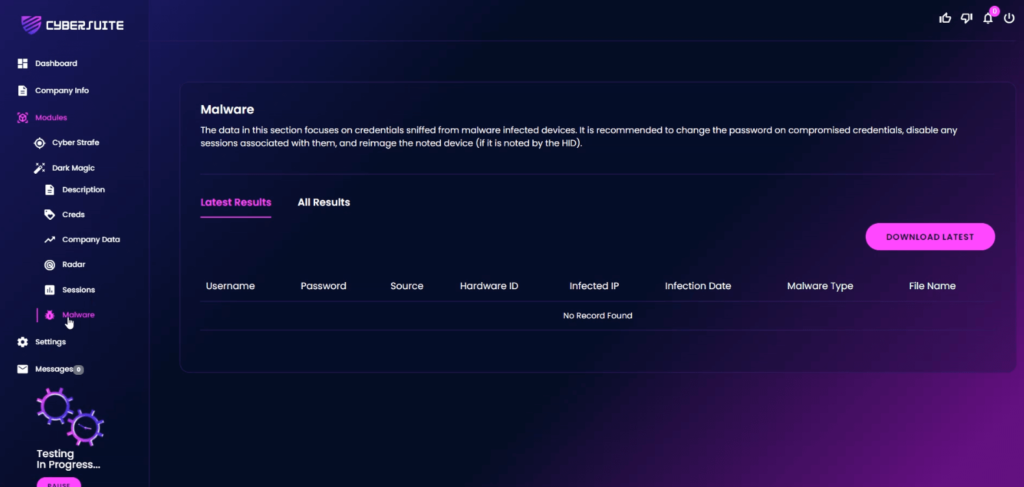
The information presented in this “Malware” section primarily revolves around the details of credentials that have been intercepted from devices infected with malware.
These credentials are vulnerable and have potentially been compromised.
In light of this, it is strongly advised to immediately change the passwords associated with these compromised credentials.
This is a crucial step in mitigating the risk of further unauthorized access and potential damage.
Furthermore, any accounts or services linked to these credentials should be temporarily disabled.
This precautionary measure is recommended to prevent the misuse of the associated accounts while the issue is being resolved.
Lastly, it is highly recommended to reimage the affected device.
Reimaging involves wiping the device clean and reinstalling the operating system and software. This process ensures the complete removal of the malware, thereby restoring the device to a safe and secure state.
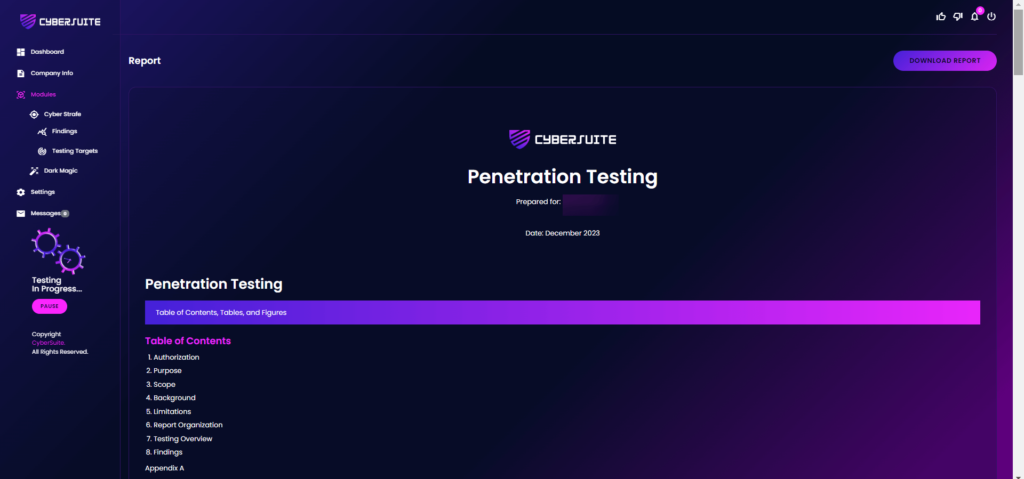
View and Download Report
For all those findings, it can be viewed and download in a single report.
To do that, go to Modules > CyberStrafe > Findings. On the top-right, click on “Report” button.
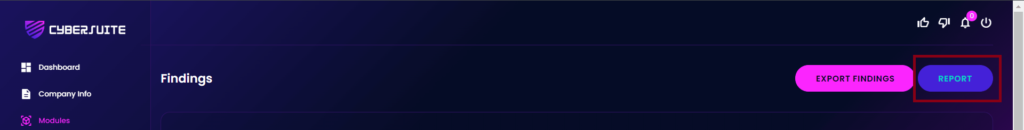
Right here, you can all findings in Cyber Strafe and Dark Magic in a single view report.
To download as a report, on top-right of the report screen, click on “Download Report”.

Open the downloaded the report (saved as PDF). You the details are very much likely as single view report like I showed you just now.
With this downloaded report, you can pass it down to whoever that require to know about the findings and take actions.
For example, you(as Security Administrator) can pass it down to your management to update current risk status of your organisation.
Or you can pass it down to your System Administrator to take necessary actions.
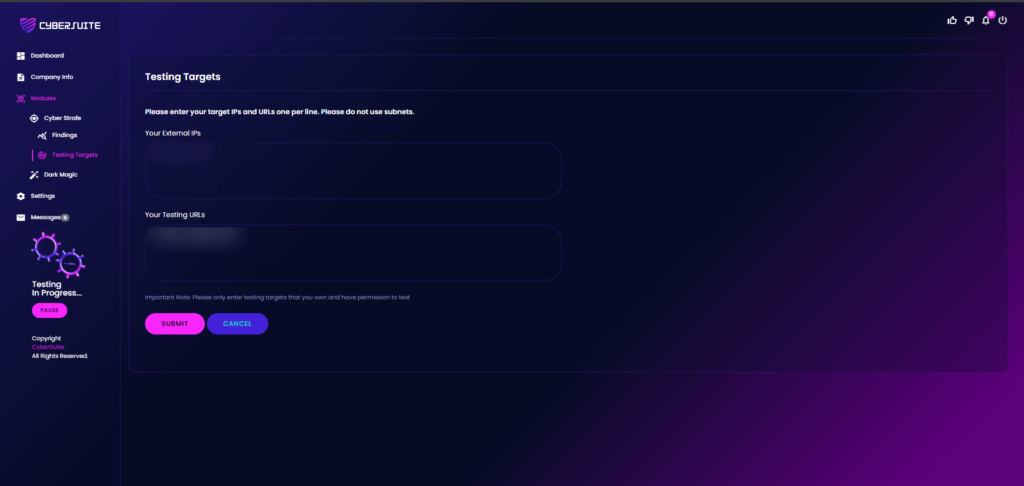
Modifying Target IPs and URLs
You can modify target IPs and URLs anytime you want as long as it’s within you license limitation.
To do that, go to Findings > CyberStrafe > Testing Targets.
What’s To Like
Apart from all the features that have been explained above, there are few other things that you may like.
24/7 continuous penetration testing and vulnerability discovery: This will ensure you will discover any vulnerability on your system.
Clean UI: The user interface is very simple and easy to navigate.
Proactively scours the dark web: Identifying stolen credentials, leaked credentials or company data, leaked session cookies or malware stealing credentials.
Reduced operational costs: By consolidating your security needs into one service, CyberSuite helps to significantly cut down on operational costs associated with managing multiple security platforms. Check the price here.
Fast and responsive support: CyberSuite’s service works round the clock, ensuring constant testing and updated results.
What’s Not To Like
What I’m saying is that I’m not a fan of the fact that IPs and URLs can’t be organized into categories or groups, such as “Finance” or “Active Directory”.
In simpler terms, you may need to do manual jobs to identify which applications or system category have most risk of all of them.
Conclusion
In conclusion for our CyberSuite Reviews, CyberSuite offers a comprehensive and robust solution for organizations looking to assess and enhance their cybersecurity posture.
With its thorough penetration testing capabilities, businesses can identify and address potential vulnerabilities before they are exploited by malicious actors.
Additionally, the dark web monitoring feature provides proactive insights into any compromised data or sensitive information that may be circulating in illicit online marketplaces.
By leveraging these advanced tools, companies can better protect their assets and customer data from cyber threats.
In today’s rapidly evolving digital landscape, investing in a proactive and reliable cybersecurity solution like CyberSuite is essential for safeguarding your organization’s reputation and bottom line. Don’t wait until it’s too late – take the first step towards fortifying your defenses today with CyberSuite<<.
IT Security / Cyber Security Experts.
Technology Enthusiasm.
Love to read, test and write about IT, Cyber Security and Technology.
The Geek coming from the things I love and how I look.