Ransomware attacks have become one of the most prevalent cyber threats in recent years, causing significant impact as they often result in downtime, loss of revenue, and reputational damage. In this article, we will explore some of ransomware attacks examples on real-world that have occurred over the past few years. Through analyzing these cases, we aim to provide insights into the tactics employed by cybercriminals in executing their malicious campaigns and highlight the importance of implementing effective security measures to prevent ransomware infections.
Ransomware Attacks Examples
- Cerber (2016)
- WannaCry (2017)
- Locky (2016)
- Petya/NotPetya (2017)
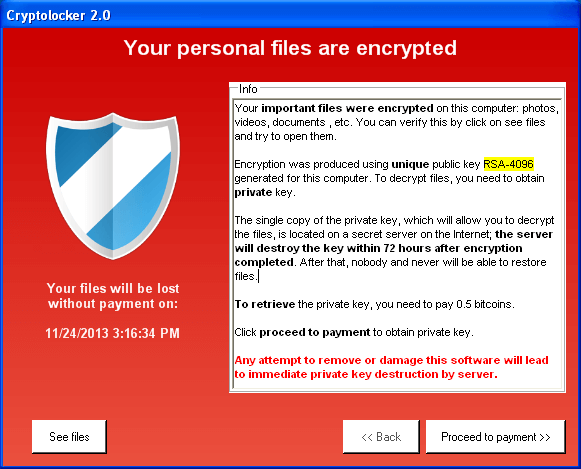
- CryptoLocker (2013)
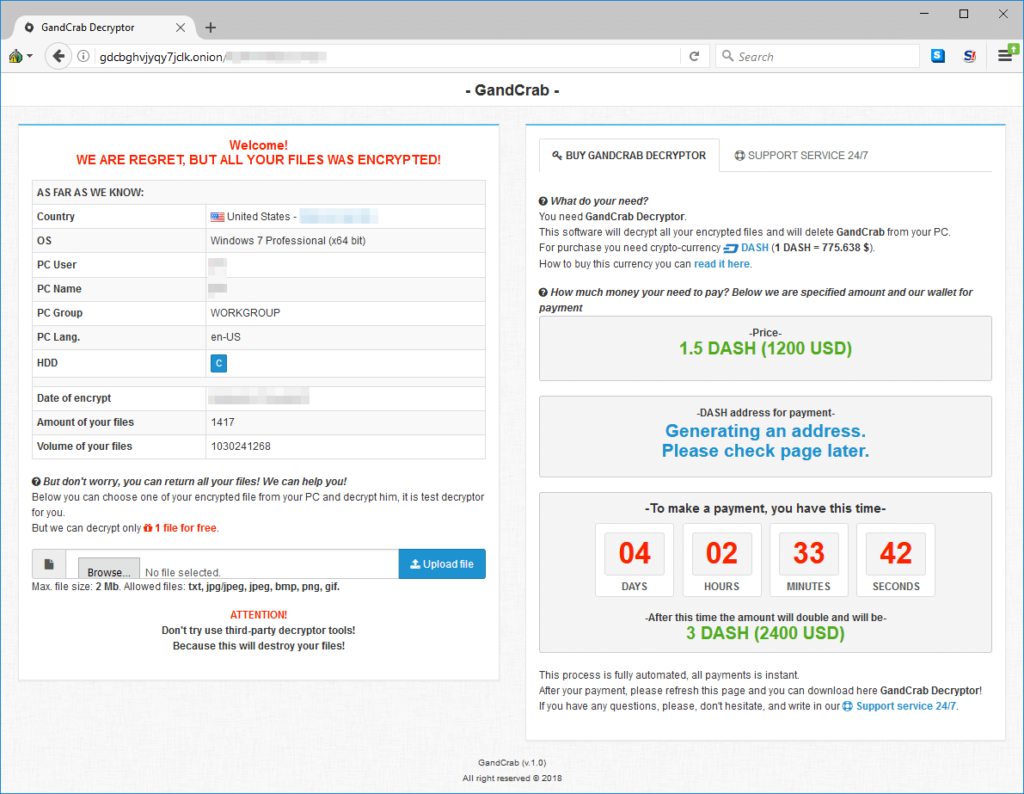
- GandCrab (2016)
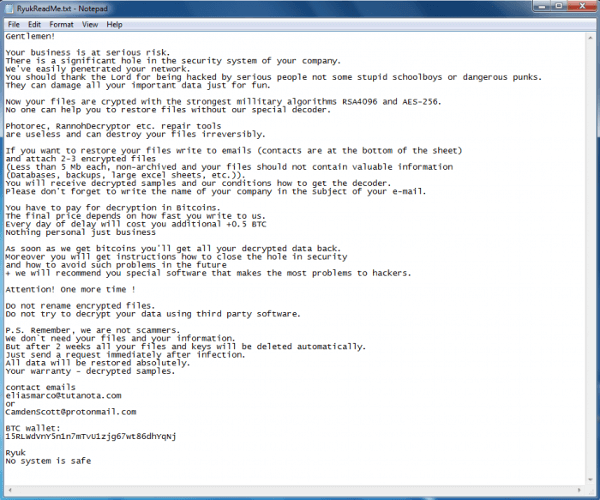
- Ryuk (2017)
- Maze (2019)
- Sodinokibi/REvil (2019)
- Dharma (2016)
- SamSam (2015)
- Bad Rabbit (2017)
- Hermes (2017)
- LockBit (2019)
- Reveton (2012)
- NetWalker (2019)
- Snatch (2018)
- Zepto (2016)
- TeslaCrypt (2015)
- Conti (2019)
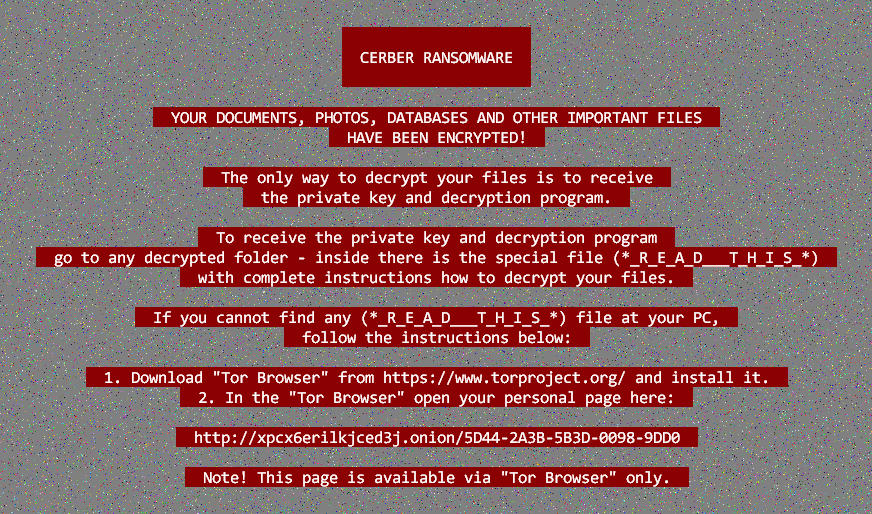
1. Cerber (2016)
Cerber ransomware was first identified in early 2016 by security researchers. The malware is distributed through phishing emails and exploit kits that target vulnerabilities in software such as Microsoft Office, Adobe Flash Player, and Java. Once installed on a victim’s computer, Cerber encrypts files using strong encryption algorithms and demands payment in exchange for the decryption key.
Cerber has evolved over time to become one of the most sophisticated and dangerous ransomware families. It uses multiple layers of obfuscation to avoid detection by antivirus software and employs anti-sandbox techniques to evade analysis by security researchers. In addition to encrypting files, Cerber can also steal personal information from infected computers, including login credentials for online banking accounts.
To deliver its ransom message, Cerber displays a warning message on the infected computer’s desktop and plays an audio file that instructs victims how to pay the demanded ransom using Bitcoin. The developers of Cerber have been known to operate a highly organized affiliate program that allows other cybercriminals to distribute the malware in return for a share of any ransoms paid by victims.
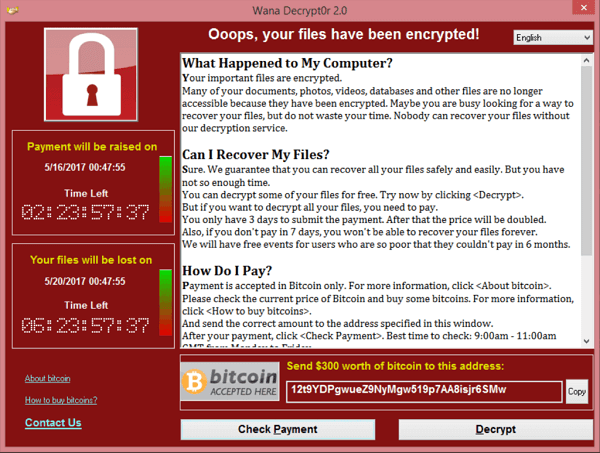
2. WannaCry (2017)
One of most famous ransomware attacks examples is WannaCry, a notorious ransomware attack that originated in May 2017, targeted computer systems running on Microsoft Windows operating systems. It is believed to have emerged from North Korea and utilized a worm to swiftly spread across networks.
The attack exploited a vulnerability in the Server Message Block (SMB) protocol called EternalBlue, which was allegedly leaked by a group known as the Shadow Brokers. By exploiting this vulnerability, WannaCry infected machines, encrypted their files, and demanded ransom payments in Bitcoin for their release. The initial demand was $300 in Bitcoin per affected device, with the ransom amount doubling after three days. If the ransom remained unpaid for seven days, the hackers threatened to delete all encrypted files.
The impact was particularly devastating as it affected critical infrastructure worldwide, including hospitals and businesses. It is estimated that the attack compromised over 200,000 computers across 150 countries before a kill switch was discovered to halt its spread.
To prevent such attacks, it is crucial to apply security patches promptly. In this case, Microsoft had released a patch, known as MS17-010, to address the vulnerability months before the attack. However, many organizations failed to install the patch, leaving their systems exposed to exploitation
3. Locky (2016)
Locky ransomware encrypts all the files on the victim’s computer and requires payment in exchange for a decryption key. It first appeared in February 2016 and quickly became one of the most widespread ransomware strains, infecting millions of computers worldwide.
The initial attack vector for Locky was through spam emails containing malicious attachments disguised as legitimate documents, such as invoices or job offers. Once opened, these attachments would download and execute the Locky malware onto the victim’s computer.
The Locky malware uses advanced encryption algorithms to encrypt all files on the victim’s computer, including documents, images, videos, and other important data. The attackers then demand payment in Bitcoin in exchange for a decryption key that can unlock the encrypted files. Despite various attempts by security researchers to decrypt Locky-encrypted files without paying the ransom, victims are still advised to exercise caution and regularly backup their important data to minimize potential damage from future attacks.
4. Petya/NotPetya (2017)
Petya/NotPetya began in Ukraine in June 2017. The malware was initially spread through a software update for a Ukrainian tax accounting program called MeDoc. The attackers were able to infiltrate the company’s systems and distribute the malware to customers who downloaded the update.
Once installed, Petya NotPetya encrypts files on the infected computer and demands payment in exchange for access to those files. However, unlike traditional ransomware attacks, Petya NotPetya had an additional feature that allowed it to spread rapidly across networks using stolen credentials. This led to widespread disruption of businesses and organizations around the world, with some estimating that over $10 billion in damages were caused by the attack.
The attack has been attributed to a group known as Sandworm, believed to have ties to Russian intelligence agencies. The incident highlights the growing threat posed by state-sponsored cyberattacks and underlines the importance of robust cybersecurity measures for both individuals and organizations.
5. CryptoLocker (2013)
CryptoLocker is one of the most well-known and destructive type of malware that began in 2013. It started as a trojan virus distributed through email attachments or malicious downloads, disguised as a legitimate file or software update. Once downloaded and activated, it would encrypt all files on the victim’s computer and demand payment in exchange for the decryption key.
The attack was highly successful due to its advanced encryption capabilities, making it nearly impossible to recover files without paying the ransom. Victims were typically given a deadline for payment with threats of permanent data loss if not met. CryptoLocker demanded payment in Bitcoin, which provided anonymity to the attackers.
The success of CryptoLocker led to numerous copycat attacks using similar tactics, leading to an increase in ransomware attacks worldwide. The attack highlighted the dangers of opening email attachments from unknown sources and emphasized the importance of regular backups and security updates.
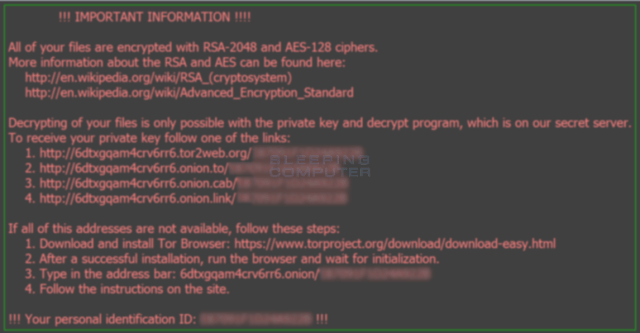
6. GandCrab (2016)
GandCrab is one of the most sophisticated ransomware that has been causing havoc since January 2018. It was first spotted in a spam email campaign that distributed malicious Word documents disguised as invoices, resumes, and other seemingly legitimate files. Once downloaded and opened, the malicious payload executes on the victim’s computer and encrypts their files with RSA-2048 encryption.
The attackers behind GandCrab have used a variety of tactics to spread their malware. They have leveraged exploit kits, compromised websites, and targeted phishing emails to deliver their payloads. Additionally, they have developed multiple versions of the attack with different levels of sophistication and capabilities.
Despite efforts by law enforcement agencies and cybersecurity firms to take down GandCrab operations, it continues to evolve and adapt its methods of attack to evade detection.
7. Ryuk (2017)
Ryuk ransomware first emerged in August 2018 and has since become one of the most dangerous strains of malware. It is believed to have originated from North Korea, with the Lazarus Group being a suspected culprit. The ransomware targets large organizations and demands high ransoms in exchange for decrypting stolen data.
The attack typically begins with phishing emails sent to employees within an organization, tricking them into clicking on a malicious link or attachment that downloads the Ryuk malware onto their device. Once inside the system, Ryuk moves laterally through an organization’s network until it finds valuable data to encrypt and hold for ransom. The attackers then demand payment in Bitcoin or other cryptocurrencies as they attempt to extort money from their victims.
Overall, Ryuk ranks among the most destructive types of ransomware, having been used to target healthcare facilities, financial institutions, and even government agencies worldwide. As such attacks continue to increase in frequency and sophistication, businesses must remain vigilant in detecting potential threats while also implementing comprehensive cybersecurity measures to protect themselves against future attacks from Ryuk or other similarly harmful malware strains.
8. Maze (2019)
Another ransomware attacks examples is Maze. The Maze ransomware first appeared in May 2019, and it quickly became famous for its unique approach to extortion. Instead of just encrypting the victim’s files and demanding payment for the decryption key, Maze also steals sensitive data from the targeted organization and threatens to release it if they refuse to pay up. This tactic called “double extortion” has made Maze particularly effective at extorting large sums of money from high-profile companies.
Maze attacks typically start with a phishing email or a compromised remote desktop protocol (RDP) connection. Once inside the victim’s network, the malware spreads laterally to other systems, using advanced techniques like living-off-the-land (LOL) tactics and fileless execution to evade detection by security tools. The attackers then use their privileged access to steal data from critical systems before deploying the ransomware payload. If the victim refuses to pay, Maze operators will publish some of this stolen information on their public website as proof of their intent and capability.
9. Sodinokibi/REvil (2019)
Sodinokibi, also known as REvil, is a prominent ransomware strain that first emerged in April 2019. It’s believed to be connected to the GandCrab ransomware group, which announced its retirement around the same time Sodinokibi appeared. This, coupled with similarities in their code and operation, has led many security researchers to conclude that at least some of the same actors were involved in both projects.
After GandCrab’s retirement, the void was quickly filled by Sodinokibi. This ransomware rapidly became infamous due to its destructive capabilities and the audacity of its attacks. It follows a “Ransomware as a Service” (RaaS) model, with its developers creating the ransomware and then leasing it to “affiliates” who carry out the attacks. The developers and the affiliates share the ransom proceeds.
Sodinokibi primarily uses the following vectors to infiltrate target networks:
- Exploiting Vulnerabilities: Sodinokibi has been known to exploit software vulnerabilities, especially in remote desktop (RDP) implementations and in enterprise VPNs, to gain unauthorized access to systems.
- Phishing Emails: These emails, often disguised as legitimate communications, contain malicious attachments or links that, when opened or clicked, lead to the ransomware being installed.
- Malicious Ads (Malvertising): By injecting malicious code into ads displayed on legitimate websites, the operators can trick users into downloading the ransomware.
Once inside a system, Sodinokibi first attempts to escalate its privileges to gain more control. It then starts to encrypt files, appending a unique extension to the filenames. The ransomware also leaves a ransom note in each affected folder, instructing the victims on how to pay the demanded ransom in exchange for a decryption key.
10. Dharma (2016)
Dharma is a ransomware that has been causing trouble for businesses globally since 2016. It was first identified in November of that year, and it quickly became one of the most popular forms of malware out there. Dharma is known for encrypting all files on a machine and demanding payment before releasing them back to their owners.
The way Dharma attacks is quite similar to other forms of ransomware: it typically spreads through phishing emails or fake software updates. Once a victim clicks on an infected link or downloads an infected file, the malware will begin encrypting files across the system. After encryption, Dharma will create ransom notes containing instructions on how to pay the attackers and regain access to locked files.
Despite its relative simplicity, Dharma has caused significant damage over the years. In 2020 alone, dozens of companies were hit by variants of this ransomware – including healthcare providers and government agencies. The best way to protect against Dharma is by regularly backing up important data and staying vigilant with email security protocols.
11. SamSam (2015)
SamSam first appeared in 2015 and was created by a group of hackers who used it to target government agencies, healthcare organizations, and educational institutions. The initial version of SamSam was distributed through spear-phishing emails that contained malicious attachments.
Once installed on a victim’s computer, SamSam would begin encrypting files and demanding payment in exchange for the decryption key. Unlike many other types of ransomware, SamSam did not rely on exploits or vulnerabilities to spread. Instead, the attackers manually infiltrated networks using stolen credentials and weak passwords.
In addition to encrypting files, SamSam also had the ability to disable antivirus software and other security measures. This made it particularly difficult for victims to recover their data without paying the ransom or resorting to costly data recovery services. Over the years, SamSam has been responsible for millions of dollars in damages across a wide range of industries and sectors.
12. Bad Rabbit (2017)
Bad Rabbit is a ransomware attack that first surfaced in October 2017. It was reported to have affected several organizations, particularly in Russia and Ukraine. The initial distribution of the malware happened through drive-by attacks where users unknowingly downloaded the malware from fake Adobe Flash installers on infected websites.
Once installed, Bad Rabbit encrypts files on the infected computer and demands a ransom payment in exchange for decryption keys. The attackers behind Bad Rabbit are believed to be linked to the same group responsible for earlier ransomware attacks, Petya and NotPetya.
The attack also had worm-like capabilities that allowed it to spread through networks by exploiting vulnerabilities in SMB (Server Message Block) protocols. This made it possible for the malware to move laterally across an organization’s network and infect other devices connected to it. The worm-like behavior of Bad Rabbit made it harder to contain than previous ransomware attacks, which relied mainly on email phishing campaigns as their primary distribution method.
13. Hermes (2017)
Hermes is a ransomware that was first discovered in 2017. It originates from the APT (Advanced Persistent Threat) group known as Lazarus, which is believed to be based in North Korea. Hermes primarily targets businesses and organizations by using social engineering tactics such as spear-phishing emails or exploiting vulnerabilities in outdated software.
Once a system is infected with Hermes, the ransomware encrypts all files on the computer and adds a “.hermes” extension to them, making them inaccessible to users. The attackers then demand payment in exchange for a decryption key that will restore access to the encrypted files. In some cases, they also threaten to publicly release sensitive information if their demands are not met.
Hermes has been responsible for numerous high-profile attacks, including one on the Taiwanese Far Eastern International Bank where they stole over $60 million. The group behind this ransomware continues to evolve its tactics and techniques in order to evade detection and maximize profits.
14. LockBit (2019)
LockBit first emerged in 2019 and quickly gained notoriety for its advanced encryption capabilities that enabled attackers to lock down entire networks. It initially spread through phishing emails with malicious attachments or links, which, once opened, would infect the device and begin encrypting files. LockBit’s developers also leveraged vulnerabilities in remote desktop protocol (RDP) to gain access to targeted systems.
Once inside a network, LockBit would move laterally across devices to encrypt as many files as possible before demanding payment for their release. The ransom demands were typically high and often reached into the millions of dollars, making it an attractive target for financially motivated cybercriminals. In recent years, there have been several high-profile attacks attributed to LockBit, including against US-based petroleum company Colonial Pipeline in May 2021.
15. Reveton (2012)
Reveton is a notorious ransomware that first surfaced in 2012. It primarily targets Windows users and is known for its aggressive tactics. The malware typically spreads through infected websites, where it masquerades as legitimate software or security updates.
Once the victim downloads and opens the file, Reveton begins to lock down the system, preventing access to files and demanding payment in exchange for restoring control. The ransom message often appears to be from local law enforcement agencies, claiming that illegal activities have been detected on the user’s computer.
To add to its scare tactics, Reveton has also been known to use webcam footage of victims as a form of blackmail. The malware has since evolved over the years with new variants continuing to emerge, making it a persistent threat in the cybersecurity landscape.
16. NetWalker (2019)
NetWalker first emerged in August 2019 as a new type of ransomware that targets businesses, government agencies, and educational institutions. It is believed to have originated in Russia or Eastern Europe and has since spread globally. NetWalker uses sophisticated techniques such as double encryption and anti-analysis features to evade detection by security software.
The ransomware attack typically begins with an email phishing campaign that tricks the victim into downloading a malicious file or clicking on a link. Once inside the system, NetWalker encrypts all files it can access including documents, images, and databases before displaying a ransom note demanding payment in Bitcoin. If the victim refuses to pay within the given timeframe, NetWalker threatens to publish or sell their data on the dark web.
NetWalker’s success has led to its rapid evolution with new variants appearing frequently. The most recent version, dubbed Mailto Ransomware, was discovered in July 2020 and features updated encryption algorithms and improved anti-detection capabilities. Its ability to cause widespread damage quickly makes it one of the most dangerous types of ransomware currently circulating online.
17. Snatch (2018)
Snatch is a type of ransomware that first emerged in late 2018. It is known for being particularly aggressive and fast-moving, with the ability to quickly infect an entire network of devices. Unlike many other types of ransomware, Snatch does not rely on phishing emails or other traditional delivery methods. Instead, it typically gains access to networks through vulnerabilities in remote desktop protocol (RDP) endpoints.
Once it has infiltrated a network, Snatch begins encrypting files and demands payment in exchange for the decryption key. In addition to locking up files on local machines, Snatch also attempts to spread to any connected devices or servers within a network. This can lead to widespread disruptions and potentially devastating consequences for businesses that are targeted by this ransomware strain. Due to its speed and aggressiveness, Snatch has been responsible for several high-profile attacks against major organizations around the world.
18. Zepto (2016)
Zepto is a ransomware that first surfaced in June 2016. It is a variant of the infamous Locky ransomware and shares many similarities with it, including the use of RSA-2048 encryption to lock down victims’ files. Zepto is typically delivered via email, often disguised as an invoice or other official-looking document. Once opened, it will begin encrypting files on the victim’s machine and appending them with the .zepto extension.
Zepto uses an AES key to encrypt its own RSA public key before sending it back to the command and control server for decryption. This makes it difficult for security researchers to obtain the private key needed to decrypt infected files without paying the ransom demanded by attackers. The amount of ransom requested varies but is usually in bitcoin, which can be difficult to trace.
Zepto also has worm-like capabilities, allowing it to spread through networks by exploiting vulnerabilities in outdated software or weak passwords. In addition, Zepto can delete shadow copies of files on Windows machines, making traditional file recovery methods ineffective. Overall, Zepto represents a significant threat to both individuals and organizations alike due to its sophisticated encryption techniques and ability to spread rapidly through networks.
19. TeslaCrypt (2015)
TeslaCrypt is a type of ransomware that first emerged in early 2015. Its initial targets were users of the popular PC game, Minecraft, but it quickly spread to other industries and platforms.
The attack typically starts with an email attachment or download containing the TeslaCrypt payload. Once installed, the malware encrypts all files on the infected computer and demands a ransom payment in exchange for a decryption key.
One unique feature of TeslaCrypt is its ability to target specific file extensions, including Microsoft Office documents and image files. This makes it particularly dangerous for businesses or individuals who rely heavily on these types of files. Despite efforts by law enforcement and cybersecurity experts, TeslaCrypt remains a significant threat to this day.
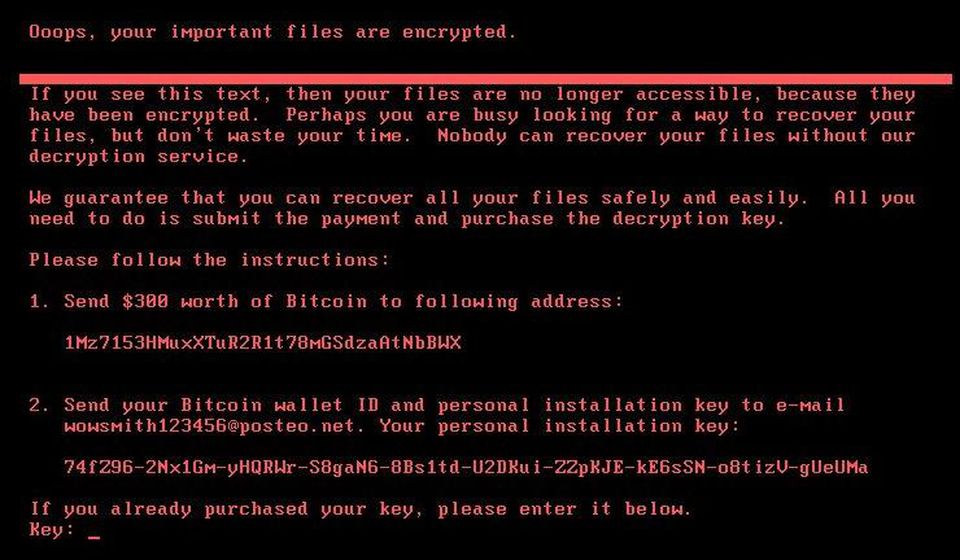
20. Conti (2019)
Conti is a relatively new ransomware that first appeared in late 2019. It quickly gained notoriety for being one of the most sophisticated and destructive strains of malware to date. Conti is a variant of Ryuk, another popular ransomware that has been responsible for several high-profile attacks in recent years.
Like other types of ransomware, Conti works by infiltrating an organization’s network and encrypting all files it can find. The attackers then demand payment in exchange for the decryption key needed to unlock the files. What sets Conti apart from other ransomware strains is its ability to spread laterally through a network, infecting multiple machines at once.
Conti uses several advanced techniques to evade detection and bypass security measures, including anti-analysis methods that make it difficult for researchers to study its code. Once it gains access to a network, it uses tools like PowerShell scripts and Mimikatz to obtain administrator-level access and move laterally through the system. This makes Conti particularly dangerous as it can quickly take over entire networks if left unchecked.
Conclusion: Ransomware Attacks Examples
In conclusion, ransomware attacks continue to pose a significant threat to individuals and organizations around the world. The examples discussed in this article highlight the devastating consequences of such attacks, ranging from financial loss to compromised data and disrupted operations.
As cybercriminals become more sophisticated and ransomware evolves, it is crucial for individuals and businesses to stay vigilant and adopt comprehensive cybersecurity measures. This includes regularly updating software, educating employees about phishing scams, and implementing robust backup systems.
By taking proactive steps to protect ourselves and our digital assets, we can reduce the risk of falling victim to ransomware attacks and contribute to a safer online environment for all.
FAQ #1: What is the biggest ransomware attacks of 2021?
Some of the most notable ransomware attacks and made headlines in 2021 include:
- Colonial Pipeline: In May 2021, a ransomware attack attributed to the DarkSide ransomware, a cybercriminal group that shut down the Colonial Pipeline, the largest fuel pipeline in the United States. The attack led to widespread fuel shortages across the southeastern United States and Colonial Pipeline ended up paying a ransom of about $4.4 million to the attackers.
- Kaseya: In July 2021, Kaseya, a company that provides software for managed IT services, targeted by ransomware called “REvil “. The attackers exploited a vulnerability in Kaseya’s VSA software to distribute ransomware to many of Kaseya’s clients, affecting between 800 and 1,500 businesses worldwide. The group initially demanded $70 million for a universal decryptor.
- JBS Foods: In June 2021, the world’s largest meat processor, JBS Foods, suffered a ransomware attack. The REvil group, also known as Sodinokibi, was again behind this attack. JBS paid a ransom of $11 million to the attackers.
- Health Service Executive (HSE), Ireland: In May 2021, Ireland’s national health service, the HSE, was hit by a ransomware attack conducted by the Conti group. The attack severely impacted healthcare services and led to widespread cancellation of appointments. The ransom demand was $20 million, but Ireland’s government stated that they did not pay any ransom.
- Acer: In March 2021, the REvil group struck again, this time targeting computer manufacturer Acer. The attackers demanded the largest known ransom at the time, $50 million, though it’s unclear if Acer paid the ransom.
- CD Projekt Red: In February 2021, the major video game developer CD Projekt Red suffered a ransomware attack in which sensitive data was stolen. The attackers threatened to leak the data if a ransom was not paid. CD Projekt Red refused to pay, and some of the data was subsequently leaked online.
FAQ #2: Are Petya and NotPetya Same?
Despite their similar names, Petya and NotPetya are not the same, though they do share some similarities. Here’s how they compare:
Petya: Petya is a piece of ransomware that was first discovered in 2016. It’s unique in that instead of encrypting specific files, it overwrites and encrypts the master boot record (MBR) of the infected system. This causes the computer to crash and, upon reboot, the victim is met with a ransom note demanding payment in exchange for the decryption key.
NotPetya: NotPetya is a destructive piece of malware that was initially thought to be a variant of Petya, hence the name. It surfaced in 2017 and, like Petya, it targets the MBR. However, there are several key differences between Petya and NotPetya:
- Purpose: NotPetya was designed primarily for destruction, not financial gain. While it presents itself as ransomware and demands a ransom from the victims, in many cases, it’s impossible to recover the files even after payment. This is because NotPetya’s encryption is designed in a way that makes it nearly impossible to reverse, leading many security researchers to classify NotPetya as a “wiper.”
- Propagation: NotPetya spreads more aggressively compared to Petya. It uses multiple propagation mechanisms, including the EternalBlue and EternalRomance exploits, which leverage vulnerabilities in Microsoft’s implementation of the Server Message Block (SMB) protocol. These exploits were used in the WannaCry ransomware attack and are believed to have been developed by the U.S. National Security Agency.
- Scope of Attack: NotPetya caused one of the most devastating cyberattacks in history, affecting businesses worldwide, with a significant impact in Ukraine. The damages from this attack were estimated to be in the billions of dollars.
So, while Petya and NotPetya share some similarities and code, they have different purposes, methods of propagation, and impacts. Therefore, they are not the same.
IT Security / Cyber Security Experts.
Technology Enthusiasm.
Love to read, test and write about IT, Cyber Security and Technology.
The Geek coming from the things I love and how I look.